Create Encryption Key
AWS Key Management Service (KMS) is a service that makes it easy for you to create and control the encryption keys used to encrypt your data. You can easily use encrypted volumes with spot instances provisioned by Spot. In order for Spot to be able to utilize your encrypted volumes, you need to grant permissions to access the custom KMS used to encrypt the volumes.
How to use custom keys with Spot
Using custom keys requires adjusting the custom keys permissions to include the spot required roles.
Step 1: Login to Your AWS KMS Console
Sign in to your AWS console and navigate to the Key Management Service (KMS) console.
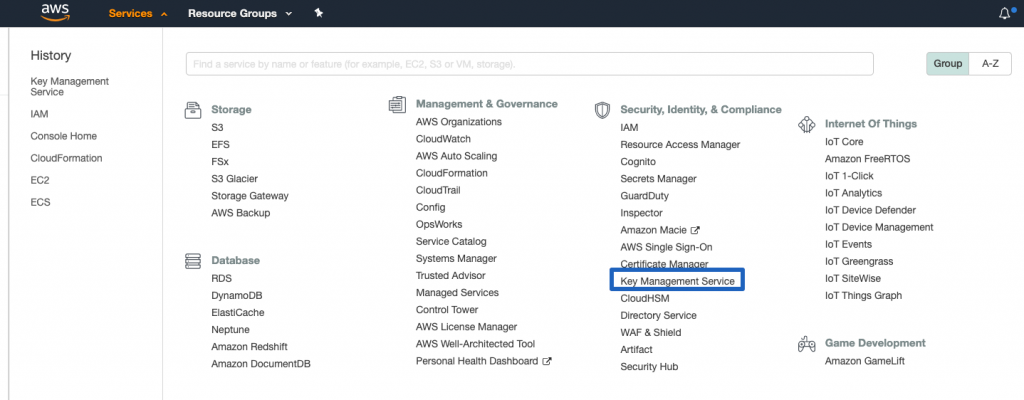
Step 2: Click on Customer Managed Keys

Step 3: Click on the Custom Key ID You Want to Encrypt Your Volumes With
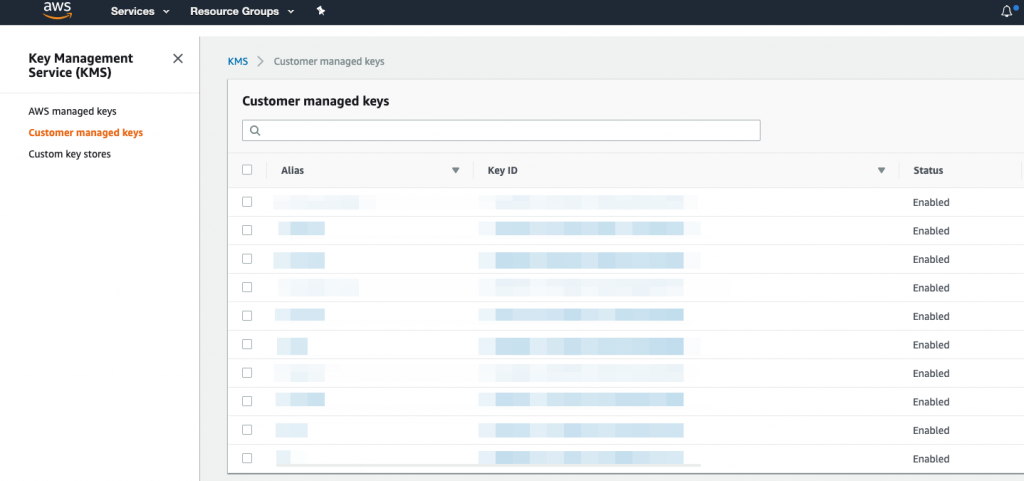
Step 4: Scroll down to Key Users
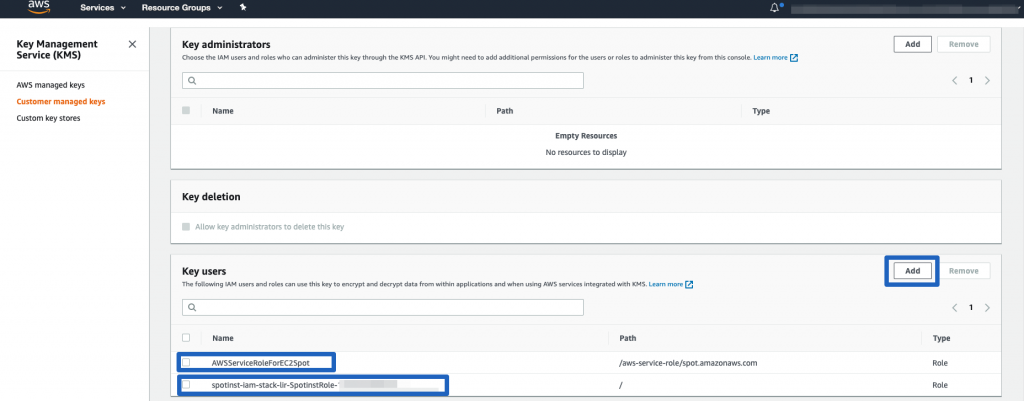
You should add two roles to this custom key:
- AWSServiceRoleForEC2Spot Linked-Service role that AWS creates automatically for each account.
- Spot cross-account IAM role The one you created when entering credentials to Spot.
You can find your Spot cross-account IAM role in the Spot settings in the Account menu.
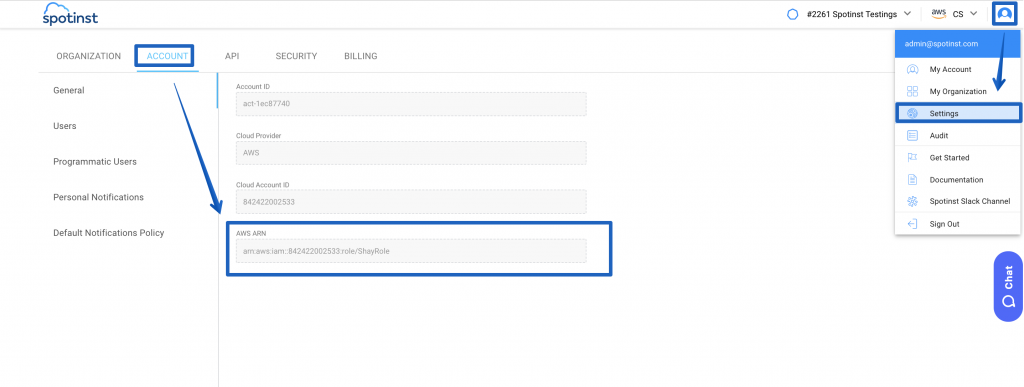
Step 5: Configuring the Key in the Elastigroup Block Device Mapping
You can add the required key to the Elastigroup block device mapping configuration.
Adding the following:
kmsKeyId – String – ID for a user managed CMK under which the EBS Volume is encrypted.
Example 1
"blockDeviceMappings": [
{
"deviceName": "/dev/sdf",
"ebs": {
"encrypted": true,
"kmsKeyId": "bajkadk-12345-1234-1234-1234567",
"volumeSize": 20
}
}
]
Example 2
In case you have a snapshot which is encrypted by the Custom KMS key:
"blockDeviceMappings": [
{
"deviceName": "/dev/xvdb",
"ebs": {
"deleteOnTermination": false,
"encrypted": true,
"snapshotId": "snap-90gh20c09281b1234",
"volumeType": "gp2"
}
}
]