Cross-Account KMS Key to Encrypt EBS Volumes
KMS Keys are fine as long as you are using a single AWS account. What if you need to use volumes from different accounts?
Let's start with a few assumptions:
- You've done the key creation as specified in Create Encryption Key.
- Account actKey will represent the account that holds the KMS key.
- Account actInst will represent the account that will run the Instances.
- Key and Instances must be in the same region
Step 1: Create a Key
-
Create KMS key in account
actKey. -
Add Account
actInstaccount number in External Accounts inside the key properties and save the changes.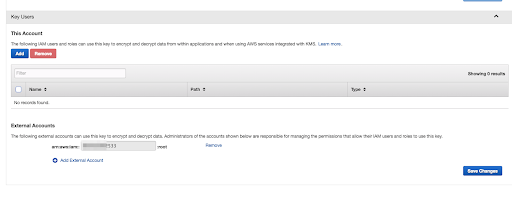
-
Switch to policy view inside the key properties, and remove the following condition, save the changes.
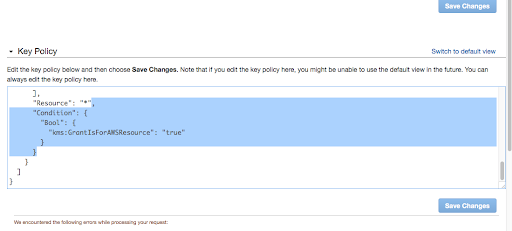
-
Save the key ARN.
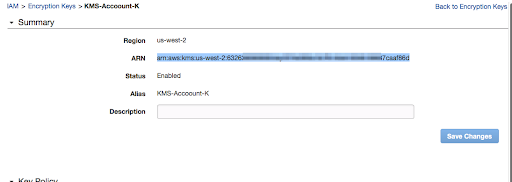
Step 2: Create Policy
Create a policy in account actInst, inserting the following JSON. Make sure to change the Key ARN:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowUseOfTheKey",
"Effect": "Allow",
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": [
""
]
},
{
"Sid": "AllowAttachmentOfPersistentResources",
"Effect": "Allow",
"Action": [
"kms:CreateGrant",
"kms:ListGrants",
"kms:RevokeGrant"
],
"Resource": [
""
]
}
]
}
Step 3: Finish Up
The next steps will be performed in account actInst using AWS CLI, note the user that your AWS CLI is configured with.
-
Attach the policy you created, to the user from the previous step.
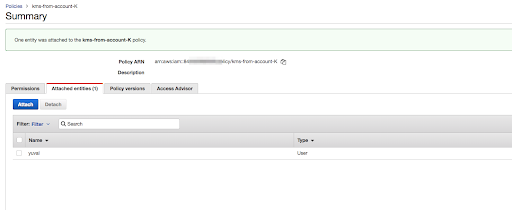
-
Copy Spot Role ARN. In the Spot console, click the user icon on the top right corner).
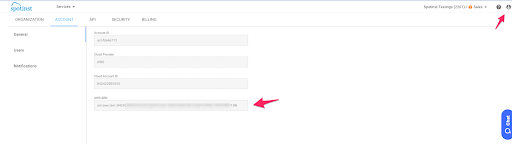
-
Run the following command in a terminal (grant for the Spot role):
aws kms create-grant --key-id <KMS KEY ARN> --grantee-principal <SPOT ROLE ARN> --operations "Encrypt" "Decrypt" "RetireGrant" "DescribeKey" "GenerateDataKey" "GenerateDataKeyWithoutPlaintext" "ReEncryptFrom" "ReEncryptTo" "CreateGrant" --name spotinst-grant -
Look for AWSServiceRoleForEC2Spot role and copy its ARN:
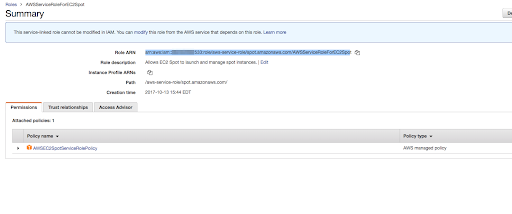
-
Run the following command in terminal (grant for the spot instances role):
aws kms create-grant --key-id <KMS KEY ARN> --grantee-principal <AWSServiceRoleForEC2Spot ARN> --operations "Encrypt" "Decrypt" "RetireGrant" "DescribeKey" "GenerateDataKey" "GenerateDataKeyWithoutPlaintext" "ReEncryptFrom" "ReEncryptTo" "CreateGrant" --name spot-grant -
You can now add your KMS key-id to the BDM section in Elastigroup's configuration:
"blockDeviceMappings": [
{
"deviceName": "/dev/sdf",
"ebs": {
"encrypted": true,
"kmsKeyId": "",
"volumeSize": 20
}
}
]